| Security Images Device | KernSafe Storage Center |
|
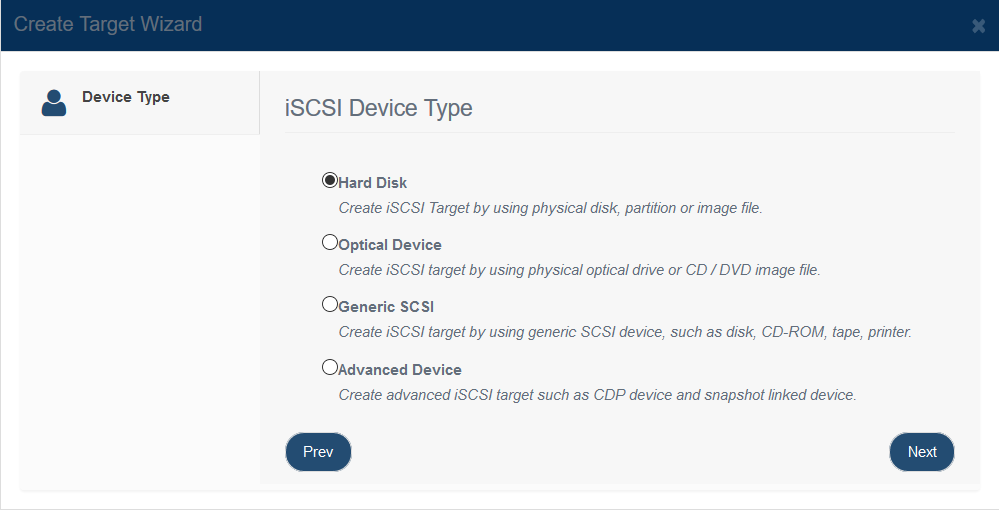
Security image file disk is very similar to image file device. However, the iSCSI security image file disks will assign one unique image file for each logon user. That means each user have their own image file to store their personal data. One user cannot access another user’s iSCSI device. This can guarantee the maximum privacy to users. Creating Security Image File Disk Device Follow the steps below to create a security image disk device: Step 1. Click New button on the top toolbar of the management system, then the Create iSCSI Target wizard popup up.
Choose Hard Disk in the iSCSI Device Type group. Press the Next button to continue.
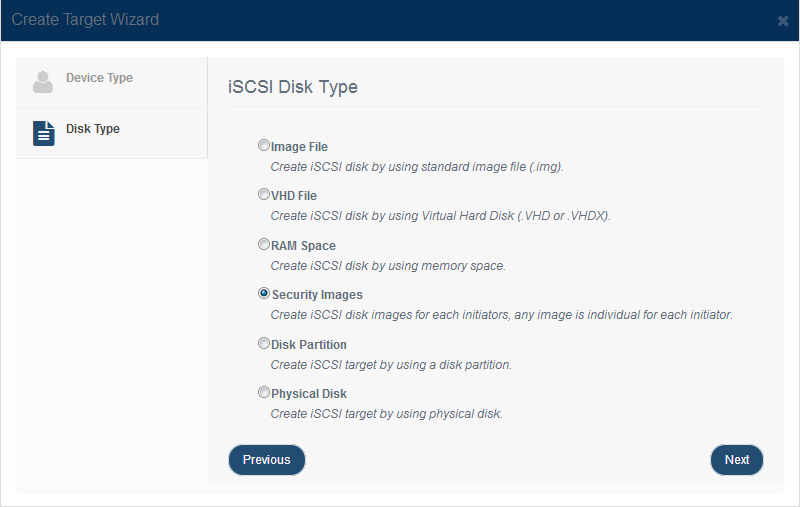
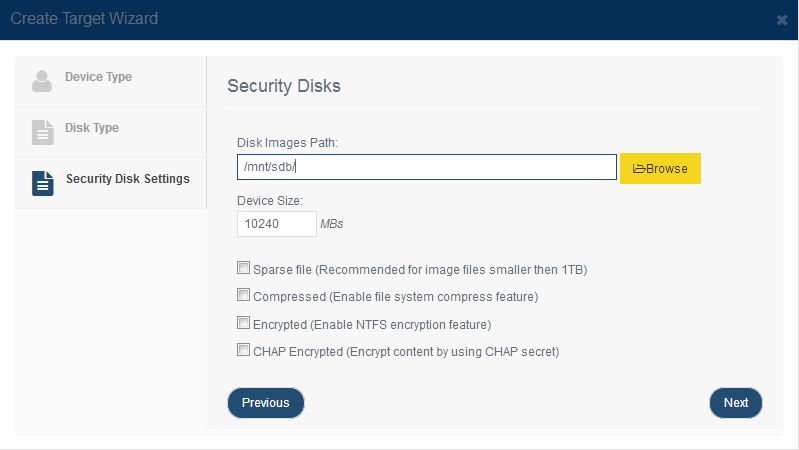
Press the Next button to continue. Step 2. Set device parameters. Creating security image file disks is also similar to creating image file disk. The difference is in the location to create the image files is a directory. KernSafe iSCSI SAN will automatically create the image file for users under the specified folder. Tab 'Browse' to select a folder to store all the image files and set the device size. Selected 'Use sparse file on NTFS file system' will save your hard disk space.
There are several options to choose from:
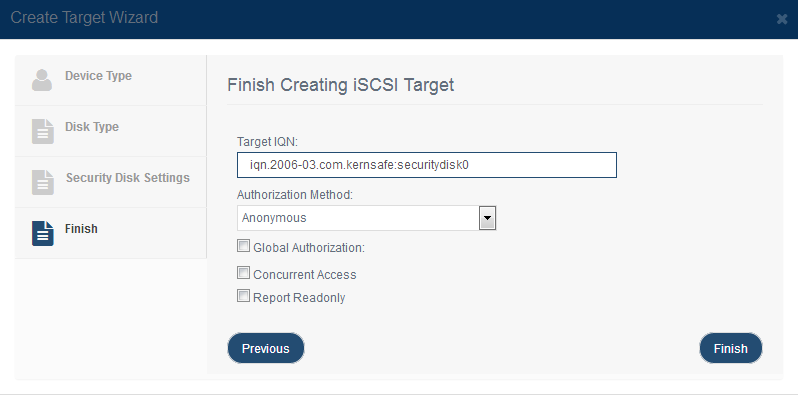
Step 3.Finish Creating iSCSI Target
Enter the Target Name. Select an authorization mode, if you don't know how to do it, you can see the topic Authorization Mechanism. Global Authorization: Indecate target will inherit authorization information (CHAP and IPFilters) from global, otherwise target will have its own authorization information. Concurrent Access: Indicate target allow concurrent read-write operations. Report Readonly: Indicate target will report as read only device if initiator don't have write access. Press the Finish button to complete iSCSI target creation. |
|
SUPPORT
- Forum
- Support Ticket
- [email protected]

- Voice Mail:
- +1 (518) 289-4888